The need for NLOS operation drives the design of the 2—11 GHz PHY. Because residential applications are expected, rooftops may be too low (possibly due to obstruction by trees or other buildings) for a clear sight line to a BS antenna. Therefore, significant multipath propagation must be expected. Furthermore, outdoor-mounted antennas are expensive, due to both hardware and installation costs. The four 2—11 GHz air interface specifications are described in the following paragraphs.
WirelessMAN-OFDM This air interface uses OFDM with a 256-point transform (see OFDM description later in this chapter). Access is by TDMA. This air interface is mandatory for license-exempt bands.
The WirelessMAN-OFDM PHY is based on OFDM modulation. It is intended mainly for fixed access deployments where SSs are residential gateways deployed within homes and businesses. The OFDM PHY supports subchannelization in the UL. There are 16 subchannels in the UL. The OFDM PHY supports TDD and FDD operations, with support for both FDD and H-FDD SSs. The standard supports multiple modulation levels including Binary Phase Shift Keying (BPSK), QPSK, 16-QAM, and 64-QAM. Finally, the PHY supports (as options) transmit diversity in the DL using Space Time Coding (STC) and AAS with Spatial Division Multiple Access (SDMA).
The transmit diversity scheme uses two antennas at the BS to transmit an STC-encoded signal to provide the gains that result from second-order diversity. Each of two antennas transmits a different symbol (two different symbols) in the first symbol time. The two antennas then transmit the complex conjugate of the same two symbols in the second symbol time. The resulting data rate is the same as without transmit diversity.
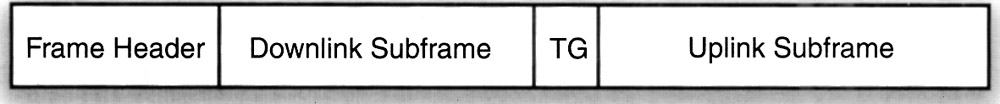
Figure 1 illustrates the frame structure for a TDD system. The frame is divided into DL and UL subframes. The DL subframe is made up of a preamble, Frame Control Header (FCH), and a number of data bursts. The FCH specifies the burst profile and the length of one or more DL bursts that immediately follow the FCH. The downlink map (DL-MAP), uplink map (UL-MAP), DL Channel Descriptor (DCD), UL Channel Descriptor (UCD), and other broadcast mes-sages that describe the content of the frame are sent at the beginning of these first bursts. The remainder of the DL subframe is made up of data bursts to individual SSs.
Each data burst consists of an integer number of OFDM symbols and is assigned a burst profile that specifies the code algorithm, code rate, and modulation level that are used for those data transmitted within the burst. The UL subframe contains a contention interval for initial ranging and bandwidth allocation purposes and UL PHY protocol data units (PDUs) from different SSs. The DL-MAP and UL-MAP completely describe the contents of the DL and UL subframes. They specify the SSs that are receiving and/or transmitting in each burst, the subchannels on which each SS is transmitting (in the UL), and the coding and modulation used in each burst and in each sub-channel.
If transmit diversity is used, a portion of the DL frame (called a zone) can be designated to be a transmit diversity zone. All data bursts within the transmit diversity zone are transmitted using STC coding. Finally, if AAS is used, a portion of the DL subframe can be designated as the AAS zone. Within this part of the subframe, AAS is used to communicate to AAS-capable SSs. AAS is also supported in the UL.
WirelessMAN-OFDMA This variant uses orthogonal frequency division multiple access (OFDMA) with a 2048-point transform. In this system, addressing a subset of the multiple carriers to individual receivers provides multiple access. Because of the propagation requirements, the use of AASs is supported.
The WirelessMAN-OFDMA PHY is based on OFDM modulation. It supports subchannelization in both the UL and DL. The standard supports five different subchannelization schemes. The OFDMA PHY supports both TDD and FDD operations. The same modulation levels are also supported. STC and AAS with SDMA are supported, as is multiple input, multiple output (MIMO). MIMO encompasses a number of techniques for utilizing multiple antennas at the BS and SS in order to increase the capacity and range of the channel.
The frame structure in the OFDMA PHY is similar to the structure of the OFDM PHY. The notable exceptions are that subchannelization is defined in the DL as well as in the UL, so broadcast messages are sometimes transmitted at the same time (on different subchannels) as data. Also, because a number of different subchan-nelization schemes are defined, the frame is divided into a number of zones that each use a different subchannelization scheme. The MAC layer is responsible for dividing the frame into zones and communicating this structure to the SSs in the DL-MAP and UL-MAP. As in the OFDM PHY, there are optional transmit diversity and AAS zones, as well as a MIMO zone.
Wireless High Speed Unlicensed Metro Area Network (WirelessHUMAN) WirelessHUMAN is similar to the aforementioned OFDM-based schemes and is focused on Unlicensed National Information Infrastructure (UNII) devices and other unlicensed bands.